Emotet, the notorious banking trojan that was first seen in 2014 and became one of the most prominent global cyber threats in the past few months, is showing no indications of slowing down. Due to a significant increase in its attack attempts, another national-level security alert has been raised.
What has happened?
The Cybersecurity and Infrastructure Security Agency (CISA) has raised another alert, warning U.S. organizations about the increasing activities of this global threat. The recent alert warns that Emotet has been targeting state and local government agencies in the U.S. Since July, around 16,000 activity alerts have been observed.
How does it operate?
Emotet is using worm-like features to infect networks. It leverages modular Dynamic Link Libraries (DLLs), allowing its operators to update and evolve its capabilities rapidly.
- The key attack vectors used by Emotet include phishing emails (with attachment and links) and brute-force attacks.
- Its C2 traffic possibly involves HTTP POST requests to Uniform Resource Identifiers. These requests are directed towards random length alphabetical directories hosted on Emotet-related domains or IPs.
Emotet’s Success Is Due to Anti-Evasion and a host of other tricks
- The ability to spread to nearby Wi-Fi networks
- A polymorphic design, meaning it constantly changes its identifiable characteristics, making it hard to detect as malicious
- Fileless infections, such as Powershell scripts that also make post-infections difficult to detect
- Worm-like features that steal administrative passwords and use them to spread throughout a network
- “Email thread hijacking,” meaning it steals email chains from one infected machine and uses a spoofed identity to respond to trick other people in the thread to open a malicious file or click on a malicious link.
Below is a diagram showing some of the techniques employed by Emotet.
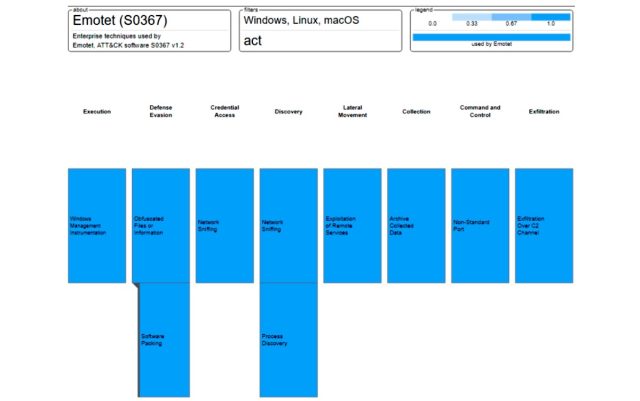
Recent attacks
Due to its frequent attack sprees, Emotet made headlines several times in the recent past.
- At the beginning of this month, malicious email campaigns were observed mimicking the Democratic National Committee and infecting the victims with Emotet malware.
- In September, some hackers targeted Quebec’s Department of Justice, infecting 14 inboxes under the Department‘s jurisdiction with a version of Emotet malware.
Endnotes
Emotet is a very active banking trojan and its operators are continuously enhancing this malware to sharpen its attacks further. For protection, CISA recommends putting strict security control over incoming emails, implementing group policy objects, and regularly reviewing firewall rules.












