Cynet’s Keys to Extend Threat Visibility
By: The Hacker News
We hear about the need for better visibility in the cybersecurity space – detecting threats earlier and more accurately. We often hear about the dwell time...
New Malware Used by SolarWinds Attackers Went Undetected for Years
By: Ravie Lakshmanan
The threat actor behind the supply chain compromise of SolarWinds has continued to expand its malware arsenal with new tools and techniques that were deployed in attacks...
Reasons Why Every Business is a Target of DDoS Attacks
By: The Hacker News
DDoS (Distributed Denial of Service) attacks are making headlines almost every day. 2021 saw a 434% upsurge in DDoS attacks, 5.5 times higher than 2020. Q3...
Ukraine Continues to Face Cyber Espionage Attacks from Russian Hackers
By: Ravie Lakshmanan
Cybersecurity researchers on Monday said they uncovered evidence of attempted attacks by a Russia-linked hacking operation targeting a Ukrainian entity in July 2021.
Broadcom-owned Symantec, in a new...
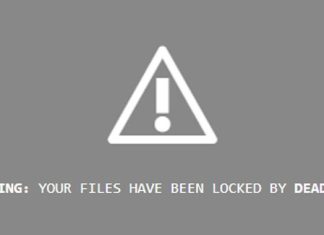
QNAP Warns of DeadBolt Ransomware Targeting Internet-Facing NAS Devices
By: Ravie Lakshmanan
Taiwanese company QNAP has warned customers to secure network-attached storage (NAS) appliances and routers against a new ransomware variant called DeadBolt.
"DeadBolt has been widely targeting all NAS...
North Korean Hackers Using Windows Update Service to Infect PCs with Malware
By: Ravie Lakshmanan
The notorious Lazarus Group actor has been observed mounting a new campaign that makes use of the Windows Update service to execute its malicious payload, expanding the...
Hackers Using New Evasive Technique to Deliver AsyncRAT Malware
By: Ravie Lakshmanan
A new, sophisticated phishing attack has been observed delivering the AsyncRAT trojan as part of a malware campaign that's believed to have commenced in September 2021.
"Through a...
Molerats Hackers Hiding New Espionage Attacks Behind Public Cloud Infrastructure
By: Ravie Lakshmanan
An active espionage campaign has been attributed to the threat actor known as Molerats that abuses legitimate cloud services like Google Drive and Dropbox to host malware...
A Trip to the Dark Site — Leak Sites Analyzed
By: The Hacker News
Gone are the days when ransomware operators were happy with encrypting files on-site and more or less discretely charged their victims money for a decryption key....
DoNot Hacking Team Targeting Government and Military Entities in South Asia
By: Ravie Lakshmanan
A threat actor with potential links to an Indian cybersecurity company has been nothing if remarkably persistent in its attacks against military organizations based in South Asia,...