More than 90% of submissions to the government’s National Vulnerabilities Database have not been analyzed or enriched since the agency announced cutbacks in February, new research shows.
The National Vulnerability Database — a critical information resource for cybersecurity defenders — has been forced to limit its operations due to funding shortages and an influx of vulnerabilities. The process known as CVE enrichment, adding public information following the creation of a vulnerability number, has been severely limited by the slowdown.
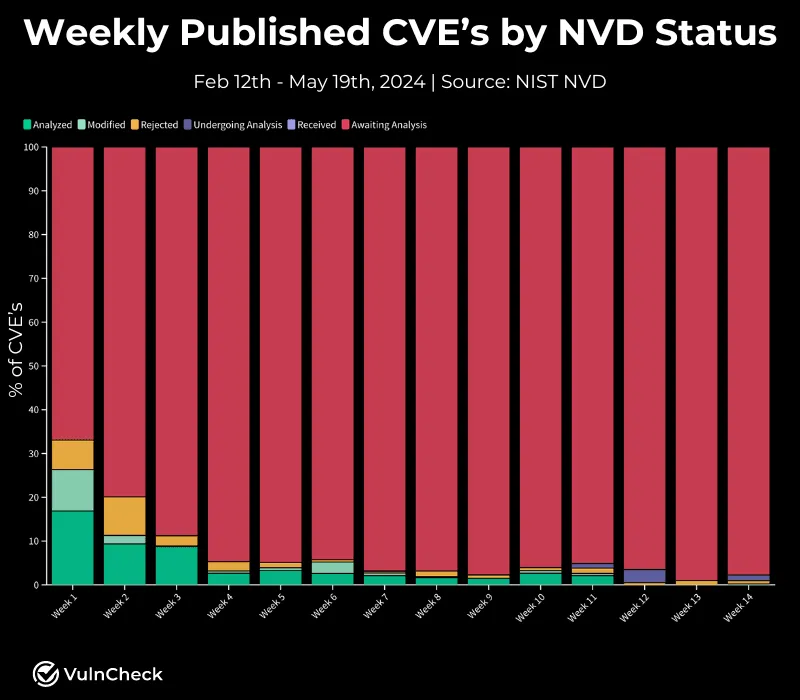
Researchers from VulnCheck analyzed the NVD’s activity since it announced cutbacks on February 12 and found that of the 12,720 new vulnerabilities added since then, 11,885 “have not been analyzed or enriched with critical data that help security professionals determine what software has been affected by a vulnerability.”
VulnCheck has a list of vulnerabilities it classifies as exploited and said nearly half of those bugs have not been analyzed by NVD since the slowdown. Another 82% of bugs that have a public proof-of-concept exploit have also not been examined, according to the company.
“Numerous prominent and influential voices in the industry have warned about how this gives malicious threat actors an upper hand in weaponizing vulnerabilities with exploits that greatly increases supply chain risks across critical sectors,” VulnCheck’s Patrick Garrity said.
“With the recent slowdown of the NIST National Vulnerability Database (NVD), it’s crucial to understand the gravity of the situation. Nation-state threat actors and ransomware gangs continue to target organizations with devastating consequences, while our own house is in disarray.”
Garrity added that for more than 20 years, NVD provided cybersecurity experts with critical information like severity scores, reference tags, vulnerability classifications and other easy-to-consume data on bugs affecting popular software.
Without this data, Garrity said, the “outlook for the NVD is bleak.”
Moving forward, cybersecurity companies will have to “fill the void” left by the NVD. Garrity suggested that the authorities allowed to create CVE numbers — the tags given to vulnerabilities — need to add more complete data about a bug to help downstream consumers.
CVE Numbering Authorities (CNAs), of which there are 379 from 40 countries, are typically cybersecurity firms, national cybersecurity agencies, technology vendors, and others.
“CVE Numbering Authorities (CNAs) should work toward enriching CVE records as completely as possible, including the submission of product names, vendor names, version numbers, thorough descriptions, broad references, CPE, CVSS, and CWE,” he said, referencing severity scores and vulnerability categorizations.
The database should also focus on automating CVE enrichment where possible as a way to close information gaps, according to Garrity, who added that the body should “deprioritize analyzing every CVE submission and move to a model where they establish trust with CNAs and the CVE program that doesn’t require a manual review of every CVE.”
Third parties should also be allowed to enrich CVE data, he noted.
The NVD said in April that it is “working to establish a consortium to address challenges in the NVD program and develop improved tools and methods.”
Two weeks ago, the Cybersecurity and Infrastructure Security Agency (CISA) acknowledged the concerns and outrage of the security community and said it is starting an enrichment effort called “Vulnrichment,” which will add much of the information described by Garrity to CVEs.
“We recently enriched 1,300 CVEs and continue to diligently work to ensure all submitted CVEs are enriched,” CISA said. “We ask all CVE Numbering Authorities (CNAs) to provide complete CVEs when making initial submission to CVE.org.”
CISA pledged to take other actions to help add information to vulnerability management processes. Lawmakers have argued that the NIST — which maintains the vulnerability database— should be fully funded to address the current issues.
Recorded Future
Intelligence Cloud.









