The website for “BravoMovies” features fake movie posters and a FAQ with a rigged Excel spreadsheet for “cancelling” the service, but all it downloads is malware.
There’s a new, fake movie-streaming service in town called BravoMovies, and the offerings are utter garbage. Despite its pretty pictures and fun-sounding titles, it’s got nothing to offer for download besides BazaLoader malware.
BazaLoader is a loader used to deploy ransomware or other types of malware and to steal sensitive data from victimized systems.
On Wednesday, Proofpoint researchers said in a report that they first observed BazaLoader in April 2020. Multiple threat actors are using the downloader, which is written in C++, to load malware such as Ryuk and Conti ransomware. As well, Proofpoint researchers said that they’re confident that there’s a “strong overlap” between the distribution and post-exploitation activity of BazaLoader and the threat actors behind The Trick malware, also known as Trickbot.
The BravoMovies campaign uses an elaborate infection chain that’s in keeping with BazaLoader affiliates, who coax their victims into jumping through a number of hoops in order to trigger the malware payloads. It starts with an email telling recipients that their credit cards will be charged unless they cancel their subscription to the service – a subscription that they never signed up for, of course.
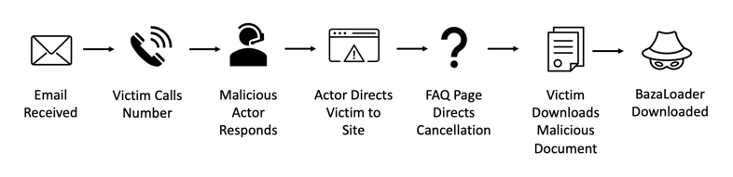
Infection chain. Source: Proofpoint
Some of the subject headers used to bait the trap:
- Your trial period M0012064753012345 is going to be expired soon. Thankfully you made a decision to stick with us!
- Demo stage is expired! Your account #M0272028060812345 will be automatically transferred to premium plan!
The email includes a phone number for a customer service line for a call center that has live humans standing by, ready to direct callers to a website where they can purportedly cancel the bogus movie-streaming service. However, the site directs those who fall for the con to instead download a boobytrapped Excel spreadsheet that will spring macros that download BazaLoader.
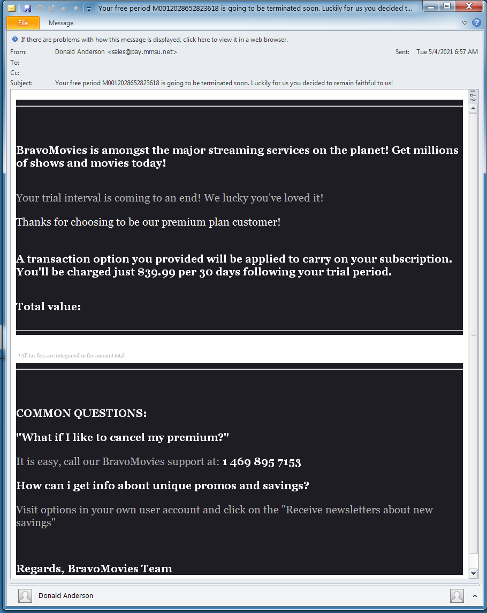
Initial BazaLoader email masquerading as an entertainment streaming service. Source: Proofpoint
Proofpoint researchers wrote that BravoMovies has the charade down pat. The fake movie-streaming service looks just like a legitimate movie and TV streaming service, complete with fake movie titles as a landing page. In fact, the threat actors jerry-rigged fake posters. “The threat actors used fake movie posters obtained from various open-source resources including an advertising agency, the creative social network Behance, and the book ‘How to Steal a Dog’”, researchers said.
The call-center operators tell their targets to visit the BravoMovies site, to pull up the Frequently Asked Questions page and to follow the directions to unsubscribe via the “Subscribtion” page. Next, they’ll be instructed to download an Excel Sheet.
The Excel sheet contains the macros that will download BazaLoader if enabled. Proofpoint researchers haven’t yet observed the second-stage payload in this campaign, they said.
One Ringey-Dingey
This isn’t the first time that Proofpoint has seen intricately composed BazaLoader email threat campaigns that have required a significant amount of human interaction – including phone-based customer service representatives – in order to trigger the malware download.
Security researchers have dubbed the call-center or live-human method “BazarCall”.
The first such use of BazaLoad spotted by Proofpoint researchers was in February 2021, when a pre-Valentine’s Day malware attack delivered lures to fake flower and lingerie stores. They’ve also seen it used in a subscription pharmaceutical services campaign.
Sherrod DeGrippo, senior director of threat research and detection for Proofpoint, told Threatpost on Wednesday that for now, the BazaLoader threat actors are the most active when it comes to using call centers as part of an attack chain. “We have also observed The Trick [also known as Trickbot] delivered by similar campaigns,” she said via email. “Phone-based threats like “tech support scams” have existed for a few years, but these threats are separate from what we’re seeing in our data. It’s a novel way of inserting a different threat vector into the attack chain.”
It’s relatively new activity for the BazaLoader threat actors, DeGrippo continued: She described the method an emerging threat that’s become more prevalent since January 2021.
More Complicated Malware Campaign = Better Evasion
Proofpoint researchers first observed the BravoMovies campaign earlier this month. They noted that its complicated nature is successful in a counterintuitive way. Namely, this campaign “demonstrates an inversely proportional relationship between successful infection rates and asking people to complete complicated steps – the more steps required by the user, the less likely they are to complete the attack chain,” they explained. “However, despite being counterintuitive, the techniques used by the threat actors in this, and similar, campaigns help bypass fully automated threat detection systems.”
For example, these techniques can help threat actors to slip past services that only flag malicious links or email attachments, they said. Similar multi-step infection chains with ample interaction from targets have been used to distribute Trickbot.
DeGrippo noted that the methods used by the BazaLoader attackers is “incredibly time consuming,” requiring significant interaction on the part of the victim in order to achieve compromise. “This is not a common method used by threat actors,” she said.
Given how gnarly these infection chains are to set up, automated threat detection systems aren’t moot, DeGrippo said. “Automated threat detection systems are incredibly useful for detecting most threats, and Proofpoint’s email-based threat detection blocks thousands of malicious emails each day,” she said. “Most threat actors are still using methods that are best identified and blocked by threat detection software.”
She pointed out that Proofpoint’s technology, for one, blocks these messages when it detects them, so they never reach the intended recipients, and the call center interaction is never made.
Proofpoint is forecasting that the threat actors behind BazaLoader and Trickbot will keep using these carefully crafted techniques in the future.
Taking Advantage of Post-COVID Cancel-itis
Also, similar to how lingerie and flowers is an email equivalent to irresistible pheromones wafting into your inbox around Valentine’s Day, cancelling streaming services plays to what Proofpoint researchers noted is a growing trend of users cancelling online entertainment following the industry’s growth spurt during the pandemic.
“Using entertainment subscription themes may be a timely and effective method for convincing users to engage with the email content and follow-on malicious documents,” the report elaborated. “During the COVID-19 pandemic in 2020, subscriptions to online streaming services skyrocketed, surpassing one billion users globally last year. But according to recent 2021 data, consumers are using fewer services while churning through free subscriptions and cancelling when their trials run out. BazaLoader threat actors are taking advantage of this human behavior trend in the identified campaign.”
How to Protect Users
In the absence of automatic threat detection systems, DeGrippo recommended training users to spot and report malicious email. “Regular training and simulated attacks can stop many threats and help identify people who are especially vulnerable,” she said. “The best simulations mimic real-world attack techniques. Look for solutions that tie into real-world attack trends and the latest threat intelligence. Regardless of the social engineering vector used, the messaging and communications are malicious. This means users and organizations need to be vigilant across all communication channels, not just traditional email or text message, but traditional mail, phone calls and internal systems as well.”
052621 06:20 UPDATE: Added input from Proofpoint’s Sherrod DeGrippo.
Download our exclusive FREE Threatpost Insider eBook, “ 2021: The Evolution of Ransomware,” to help hone your cyber-defense strategies against this growing scourge. We go beyond the status quo to uncover what’s next for ransomware and the related emerging risks. Get the whole story and DOWNLOAD the eBook now – on us!












