Attackers can take advantage of the fact these apps access, gather, store and transmit more information than any other app their victims have installed.
Android stalkerware apps – used to surreptitiously track people’s movements and digital activities – turn out to themselves be rife with security holes that put victims in even danger.
Stalkerware can track the GPS location of a victim’s device, record conversations, capture images and snoop on browser histories. And overall, according to ESET researcher Lukas Stefanko, the apps access, gather, store and transmit more information than any other app their victims have installed.
“During our research, we identified that some stalkerware keeps information about the stalkers using the app and gathered their victims’ data on a server, even after the stalkers requested the data’s deletion,” he explained in an analysis on Monday.
While the apps store and transmit all that data, they often unfortunately do so without proper data protection, according to ESET. In an investigation, the firm’s researchers found more than 150 security issues in 58 Android stalkerware apps.
“This analysis identified many serious security and privacy issues that could result in an attacker [separate from the stalker] taking control of a victim’s device, taking over a stalker’s account, intercepting the victim’s data, framing the victim by uploading fabricated evidence or achieving remote code execution on the victim’s smartphone,”
Some of the stalkerware app bugs that the firm’s researchers found included:
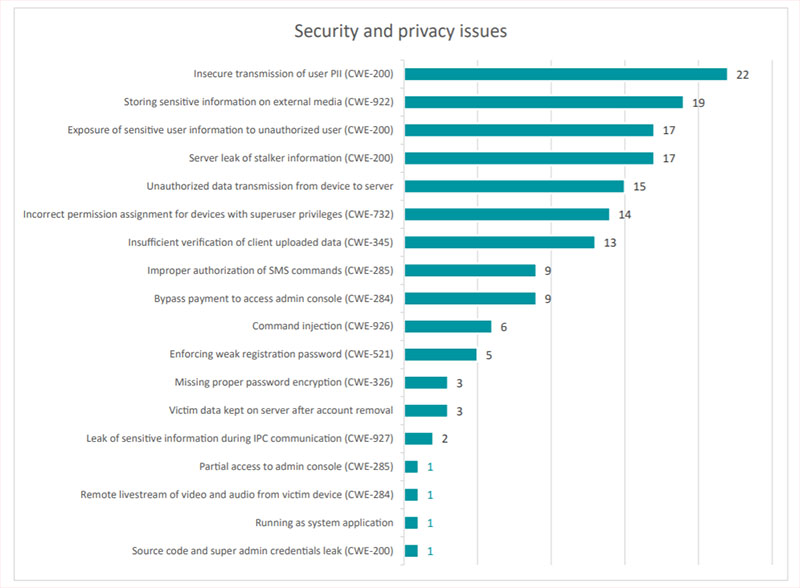
Breakdown of security and privacy issues uncovered in ESET’s research.
ESET reported the issues to the affected vendors, but only six decided to address the flaws. Forty-four never replied, seven promised to patch in an upcoming update, and one actively decided not to fix the reported issues.
The most common issue that researchers identified was insecure transmission of victim and stalker personally identifiable info (PII), found in 22 of the analyzed stalkerware apps.
“Sensitive victim and/or stalker information was transmitted from victim devices to the stalkerware servers over the unencrypted HTTP protocol and was not further protected,” according to the report.
“An attacker on the same network could intercept network traffic and steal or change transmitted data. Because of that, it would be possible to obtain admin credentials, all uploaded data such as text messages, call log, contact list, keystroke logs, browsing history, recorded phone calls, pictures, screenshots or even replace downloaded binary files that will be executed without integrity check. As a result, the attacker could take over the stalker’s account, access the victim’s private information and trigger remote code execution.”
Another widespread issue, found in 17 of the apps, involved servers exposing the user data stored on them, either through open directory listings or predictable names.
“It would be possible for an attacker to access what seem to be recorded calls, photos, email addresses, IP logs, IMEI numbers, phone numbers, usernames, addresses, call logs, text messages, Facebook and WhatsApp messages, GPS locations or even source code and backups and other data without any authentication,” according to ESET.
Stalkerware on the Rise
This app advertises itself as a personal safety utility. Source: ESET
Unfortunately, the pool of people affected by this state of affairs is widening: According to ESET stats, there were almost five times more Android stalkerware detections in 2019 than in 2018, and in 2020 there were 48 percent more than in 2019. That dovetails with an earlier analysis from Kaspersky finding that volumes are on the rise.
Even though Google banned stalkerware apps from Google Play last year, plenty of offerings get around that barrier by purporting to be a legitimate utility – antitheft applications, for instance, or tools for monitoring employees or children. Some even claim to be safety apps for women.
In third-party marketplaces, these kinds of apps are easy to find, Stefanko said. “The word ‘spy’ is used many times on their websites,” he explained. “Searching for these tools online isn’t difficult at all; you don’t have to browse underground websites.”
When it comes to installation, the apps aren’t delivered in the same way as other malware; it can’t be sent via a sneaky email or installed in some other remote way.
“Generally, the stalker needs to have physical access to a victim’s device so as to side-load the stalkerware,” Stefanko said. “Because of this, stalkers are usually someone from the close family, social or work circles of their victims.”
However, the installation only takes two minutes, according to ESET.
Download our exclusive FREE Threatpost Insider eBook, “2021: The Evolution of Ransomware,” to help hone your cyber-defense strategies against this growing scourge. We go beyond the status quo to uncover what’s next for ransomware and the related emerging risks. Get the whole story and DOWNLOAD the eBook now – on us!












