Researchers have highlighted tactics used by fraudsters today in voice-based phishing campaigns.
Phishing attempts involve fraudulent messages sent over email, social media networks, SMS, and other text-based platforms. They may appear to be from your bank, popular online services — such as PayPal or Amazon — or they may attempt to lure in victims with promises of tax rebates and competition prizes.
These messages often contain malicious attachments designed to deploy malware, or they may try to direct victims to fake websites.
So-called “vishing” is a subset of phishing techniques that combines ‘voice’ and ‘phishing’. Victims may be cold-called or emails could contain phone numbers, voice notes, and messages — but the overall goal is the same: to swipe your personal data.
Scam artists can employ “spray and pray” techniques in campaigns and blast out thousands of emails in one go, and now, voice over internet protocol (VoIP) technology has allowed fraudsters to do the same, all while spoofing their caller IDs and identities.
In separate case studies published by Armorblox on Thursday, the team highlighted two Amazon vishing attacks intent on stealing customer credit card details — and how the use of voice messages can bypass existing spam filters.
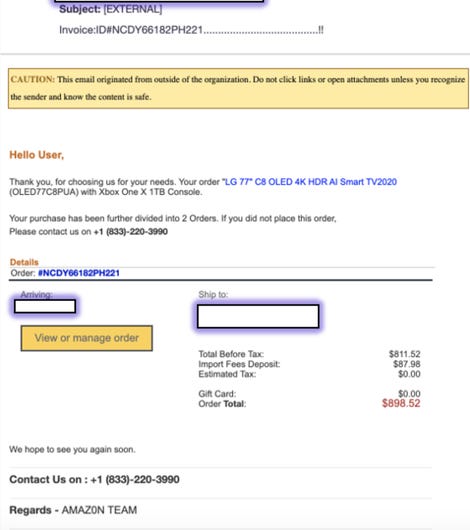
The first example vishing attempt, tracked to roughly 9,000 email inboxes, was sent from a Gmail account and contained the subject line: “Invoice:ID,” followed by an invoice number and content containing color markers used by Amazon.
This email says that an order for a television and gaming console had been placed — a purchase worth hundreds of dollars — and urges the recipient to contact them using a phone number if there are any errors.
Armorblox
Armorblox called the ‘payload’ phone number and a person on the other end of the line answered, pretending to be from Amazon customer service. The scammer requested the order number, customer name, and credit card details before cutting the call and blocking the number.
According to the researchers, the use of a zero in “AMAZ0N TEAM” helped the message bypass existing spam filters, including Microsoft Exchange Online Protection (EOP) and Microsoft Defender for Office 365 (MSDO). A spam level of “1” was assigned to the email, which means that the message was not considered fraudulent.
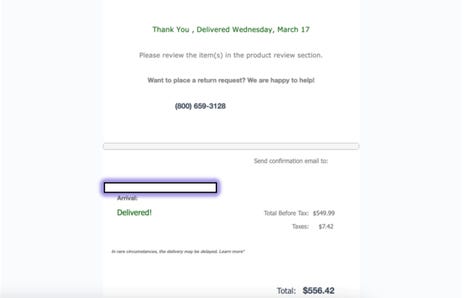
In the second example, which reached roughly 4,000 inboxes and was also able to circumvent EOP and MSDO, fraudsters impersonated Amazon via a spoofed email address — “no-reply@amzeinfo[.]com” — and used the subject line, “A shipment with goods is being delivered.”
The email contained an order number, a payment amount of $556.42, and another phone number ‘payload’ for customers to make return requests. However, in this case, the researchers found that the scam appeared to have been shut down as the phone number was not in service.
As the emails did not contain malicious attachments or links, this allowed the fraudsters to bypass spam filters.
In both cases, the fraudsters used a combination of social engineering, brand impersonation, and emotive triggers — the apparent loss of hundreds of dollars — to induce victims into calling them. If successful, victims could end up handing over their personal data and credit card details, leading to consequences such as identity theft or fraudulent payments made on their behalf.
As many of us remain at home due to the pandemic and we’ve come to rely more heavily on online shopping, fraudsters will continue to try and exploit these trends. In August, the FBI and US Cybersecurity and Infrastructure Security Agency (CISA) issued a joint advisory warning of an increase in vishing attacks against the private sector.
Previous and related coverage
Have a tip? Get in touch securely via WhatsApp | Signal at +447713 025 499, or over at Keybase: charlie0











