2021 was a record year for the number of zero-day flaws in Chrome that attackers were exploiting before Google knew about them. Is Google losing the race against attackers?
According to Google Project Zero’s zero-day tracker, there were 25 browser zero-days patched last year, of which 14 were for Chrome, six were for Safari’s WebKit engine, and four were for Internet Explorer. In 2020, there were just 14 browser zero-day flaws, of which more than half were in Chrome. But between 2015 and 2018 there were no Chrome zero-day exploits in the wild, according to the tracker data.
Adrian Taylor, a technical program manager on the Chrome Security Team, says in a blogpost that the increase in browser zero-days “may initially seem concerning” and “could point to a worrying trend”. But he argues it could be a good thing because it means more zero-days are being caught and fixed.
SEE: Cybersecurity: Let’s get tactical (ZDNet special report)
In other words, interpreting trends in zero-day data – such as the suggestion there was no zero-days between 2015 and 2018 – is difficult because it only includes ones that are now known about and hopefully fixed. There are likely more undiscovered ones being used out there.
“We don’t believe there was no exploitation of Chromium based browsers between 2015 and 2018,” notes Taylor.
“We recognize that we don’t have full view into active exploitation, and just because we didn’t detect any zero-days during those years, doesn’t mean exploitation didn’t happen. Available exploitation data suffers from sampling bias.”
That’s similar to a conclusion about zero-days that Google’s Threat Analysis Group (TAG) made last year: “There is not a one-to-one relationship between the number of 0-days being used in-the-wild and the number of 0-days being detected and disclosed as in-the-wild.”
Still, there were a lot of zero-day exploits discovered in 2021. Taylor offers four reasons for this. First, browser makers today are more transparent about bugs being exploited in the wild than in the past. Google Project Zero – which gives vendors 90 days to fix a bug before publicly disclosing it – has helped normalize this behavior from major software vendors.
Another factor is the demise of the Adobe Flash Player desktop browser plugin, which used to be the top target for attackers in 2015 and 2016, but browser makers and Adobe dropped support for it on December 31, 2020.
“As Flash is no longer available, attackers have had to switch to a harder target: the browser itself,” writes Taylor.
On top of that is the popularity of open source Chromium used by Brave, Opera, Vivaldi and so on. While Edge isn’t anywhere near as popular as Chrome, it does ship with Windows 10 and Windows 11.
“Attackers go for the most popular target. In early 2020, Edge switched to using the Chromium rendering engine. If attackers can find a bug in Chromium, they can now attack a greater percentage of users,” argues Taylor.
Yet another cause for the apparent rise in browser zero-days is that due to efforts to harden the browser, such as Chrome’s site isolation, attackers need to chain together multiple bugs to actually exploit a browser. So, attackers need more ammunition for the same effect.
“For exactly the same level of attacker success, we’d see more in-the-wild bugs reported over time, as we add more layers of defense that the attacker needs to bypass,” he notes.
SEE: How Russia’s invasion of Ukraine threatens the IT industry
Finally, browser software is vast and now almost as complex as an operating system.
“More complexity means more bugs,” Taylor comments.
He also points to Project Zero’s recently published research on how quickly software vendors patch flaws. Chrome was patched and released faster than WebKit and Firefox.
Google is urging all vendors to implement a more frequent patch cadence for security issues. Chrome, for example, cut its stable release cycle from six weeks to four weeks. Microsoft is implemented the same cycle for Edge from version 94’s release in September.
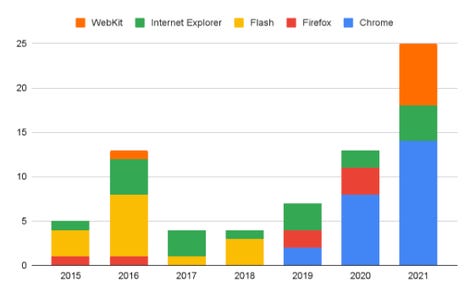
Project Zero has tracked all zero-days for browsers.
Image: Google












