Could the leak spell doom for former customers of the illicit data brokerage WeLeakInfo?
A user on a popular hacker forum is selling a database containing highly sensitive information of more than 24,000 customers of the now-defunct illegal online service WeLeakInfo.
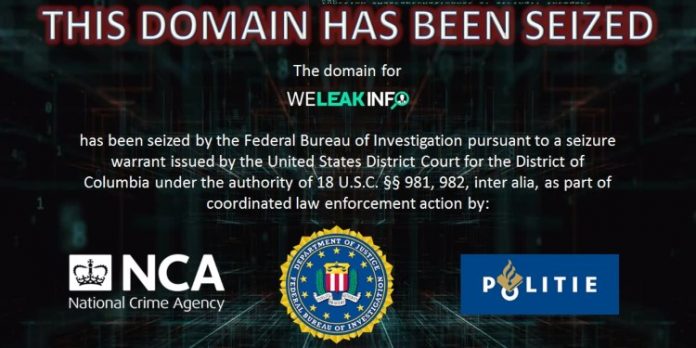
Before it was shut down by the FBI in January 2020, WeLeakInfo was a website that had been selling access to stolen information scraped from more than 10,000 data breaches, which contained over 12 billion indexed user credentials, including names, usernames, email addresses and passwords for online accounts.
The forum user is selling the highly sensitive information of former WeLeakInfo customers – including their full names, IP addresses, street addresses, and phone numbers – for about $2 in virtual forum currency.
For the customers who used their real names and personal payment accounts to make the illegal purchases, this leak, if genuine, is tantamount to doxxing.
To see if any of your online accounts were exposed in previous security breaches, use our personal data leak checker with a library of 15+ billion breached records.
What was leaked?
The author of the forum post is selling a ZIP archive that contains payment data of WeLeakInfo customers who made their illicit purchases via Stripe, including:
- Full names
- Partial credit card data
- Transaction dates and their Stripe reference numbers
- Currencies and amounts paid for stolen data
- Email addresses
- IP addresses
- User Agents (used to identify the browser/device used by the customer)
- Street addresses
- Phone numbers
Contents of the WeLeakData ZIP archive:
Stripe dashboard data included in the WeLeakData samples:
Examples of Stripe payment information included in the WeLeakData samples:
Fortunately for the people who bought illicit data from WeLeakInfo via PayPal or Bitcoin, their information is not included in the leak. In the words of the author, they’re “all good.”
How the data was acquired: an oversight by the FBI?
The user who is selling the WeLeakData archive on the hacker forum claims that the FBI might have missed a spot during the seizure of the original WeLeakInfo domain. According to the forum post author, there was a separate domain associated with the WeLeakInfo service that was used to process payments made by people who bought stolen data via Stripe. And it seems that the payment website was, inadvertently or not, allowed to expire in March 2021.
This means that after the website expired, anyone could have claimed the domain as their own. Which the cheeky forum user seemingly did on March 11.
The author claims they were then able to perform a password reset against the Stripe.com account that was potentially associated with one of the two owners of WeLeakInfo, and gain access to all the data from the website, which seems to have operated for less than a year and accumulated sales of a little over £100,000 from 24,603 customers.
Judging from the samples of data provided by the author, the age of the Stripe account owner is consistent with the FBI’s information about the arrested owners of WeLeakInfo.
What’s the impact of the leak?
The information found in the WeLeakData archive could come back to bite the website’s former users in a variety of ways.
First and foremost, threat actors could use the data to identify the users and blackmail or extort them, or try to breach their other online accounts via social engineering. The latter, however, would probably be unlikely to succeed as people who know where to purchase illicit information are usually quite adept at protecting their own data.
On the other hand, could this spell doom for more than 24,000 users whose personal details are now accessible to law enforcement agencies? Back in January 2021, a year after the website was seized, the UK’s National Crime Agency arrested 21 people across the country as part of an operation targeting former WeLeakData customers, which means that law enforcement already had data on at least some of the customers. Could this number grow a thousand-fold this year?
So, next time you see an ‘accounts for sale’ ad somewhere on the web, it’s worth keeping in mind that not every service you can buy online is legal: always make sure you’re not breaking the law when buying any kind of information or data.
The importance of safe domain hygiene
For organizations on the legitimate side of business, leaks like this show why detaching your domain from all of your online accounts is incredibly important. This is especially true if you’re switching to a different domain.
If you don’t want to wake up to see confidential company data sold on some hacker forum, make sure to keep tabs on your domain expiry dates. Otherwise, someone can snatch your domain on the day of expiry, take it over and access all of the accounts attached to it.