McAfee has uncovered a vulnerability in Peloton’s Bike+ line and Tread exercise equipment that would give an attacker full, unnoticed access to the device, including its camera and microphone.
McAfee worked with Peloton in March to fix the issue and Peloton has since released an update that solves the vulnerability.
In a blog post, McAfee’s Advanced Threat Research team researchers Sam Quinn and Mark Bereza explained that the flaw was with the bike’s Android Verified Boot process, which they said was initially out of scope and left the Peloton vulnerable.
Quinn and Bereza shared a video of their work demonstrating how they were able to bypass the Android Verified Boot process and compromise the Android OS.
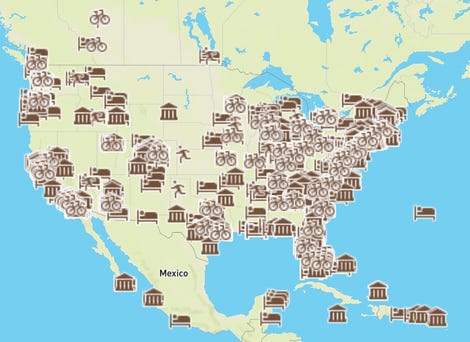
The blog describes a variety of ways the vulnerability could have been used by attackers with physical access to a Bike+ or Tread exercise equipment. The researchers included a map that lists all of the publicly available Peloton equipment available in spaces like gyms, hotels, apartment complexes, and even cruise ships.
PeloBuddy
“A worst-case scenario for such an attack vector might involve a malicious agent booting the Peloton with a modified image to gain elevated privileges and then leveraging those privileges to establish a reverse shell, granting the attacker unfettered root access on the bike remotely. Since the attacker never has to unlock the device to boot a modified image, there would be no trace of any access they achieved on the device,” Quinn and Bereza wrote.
“This sort of attack could be effectively delivered via the supply chain process. A malicious actor could tamper with the product at any point from construction to warehouse to delivery, installing a backdoor into the Android tablet without any way the end user could know. Another scenario could be that an attacker could simply walk up to one of these devices that is installed in a gym or a fitness room and perform the same attack, gaining root access on these devices for later use.”
There were even ways for attackers to make their presence permanent by modifying the OS, putting themselves in a man-in-the-middle position. In this case, an attacker would have full access to network traffic and SSL encrypted traffic using a technique called SSL unpinning, the blog explained.
“Intercepting and decrypting network traffic in this fashion could lead to users’ personal data being compromised. Lastly, the Peloton Bike+ also has a camera and a microphone installed. Having remote access with root permissions on the Android tablet would allow an attacker to monitor these devices and is demoed in the impact video [above],” the researchers said.
The simplicity of the vulnerability prompted Quinn and Bereza to reach out to Peloton, which later discovered that the problem extended beyond just the Bike+ to the Tread exercise equipment.
The company released a fix for the problem that no longer allows for the “boot” command to work on a user build, mitigating this vulnerability entirely, according to the researchers.
Adrian Stone, Peloton’s head of global information security, said that if an attacker is able to gain physical access to any connected device in the home, additional physical controls and safeguards become increasingly important.
“To keep our members safe, we acted quickly and in coordination with McAfee. We pushed a mandatory update in early June and every device with the update installed is protected from this issue,” Stone added.