Insider threats are a serious and growing problem. According to recent research, malicious employees contribute to 20% of incidents and the attacks that insiders are involved in are, on average, 10 times larger than those conducted by external actors. Further data (PDF) has shown an increase in insider threat attacks over the past two years, as the risk has been exacerbated by the remote working through the pandemic.
To minimize insider threats, all organizations should monitor marketplaces, forums, and social media channels for chatter about their company. This helps them to spot the early warning signs of an imminent attack, such as cybercriminals looking for insider knowledge, or disgruntled employees making unsavory comments. This monitoring must also extend to the Dark Web, as this is a gold mine for cybercriminal reconnaissance on organizations, because threat actors believe that they’re out of the reach of law enforcement and cybersecurity teams.
Types of Insider Threat
When we talk about insider threats it is important to understand that there is more than one type of malicious insider. Broadly, you can categorize them in three groups:
Insiders motivated by financial gains: In the current economic climate, employees can be nudged into malicious activity by threat groups. For example, the threat group Lapsus$ infamously posted a recruitment call for help from employees in telecom companies, software and gaming corporations, and call centers — offering money in exchange for information.
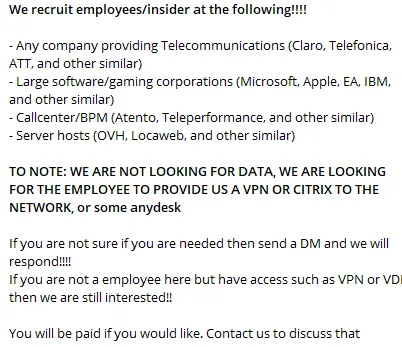
Loners and opportunistic threat actors: These are hard-to-spot insiders who use their privileged position in the network to harm the company. While they’re statistically less common, they can have a severe impact on an organization when they do strike. For example, the New York Post employee who took an ax to the company’s reputation recently by posting offensive messages on its corporate Twitter account. Dark Web analysis can help to spot these malicious actors if and when they publish an inquiry or ask for help on specific issues they face when navigating around the corporate environment. They can also be spotted offering to sell insider information on the Dark Web.
Innocent insiders: These can also unwittingly harm the company by being involved in threat activity without their consent or knowledge. According to research, employees are more than twice as likely to make an error and click malicious links, rather than to maliciously misuse their access.
That’s who you’re up against, but it’s also important to understand what malicious actors could be looking for, inquiring about, or selling.
Threat Modeling for Insider Threat
Companies threat modeling for malicious insiders need to identify where their infrastructure is the most insecure, what assets they have that are the highest value, and which tactics are most regularly used by threat actors. Insight into the Dark Web can help the organization establish how criminals go about their reconnaissance and use malicious insiders, which can help inform their defenses.
The most popular method used to gain access to a company’s environment is obtaining and utilizing leaked credentials. But apart from basic “password and username” sales, businesses also need to look out for cookie-session leaks for apps such as Slack and Teams, which threat actors can use to socially engineer their way into the company and abuse the trust of an employee.
Another aspect that companies need to be conscious of are trigger events that increase the likelihood of a company being targeted for attack. For example, if an oil company is set to announce its annual revenue during a cost-of-living crisis, the organization must assess the animosity level from employees, ex-employees, and outsiders reacting to the announcement. The revenue reveal, in this example, is a potential trigger event, requiring the business to be particularly diligent in monitoring the Dark Web for any chatter around the company before, during, and after the event. In cases like these, companies must ask themselves whether they should implement extra defenses or apportion additional resources.
During trigger events, companies could potentially spot malicious insiders by monitoring an uptick in alerts or irregular online activity. Connections between a company device and the Tor network are a very reliable data point for discovering an insider threat, because there is virtually no good reason why an employee would be connecting to the Dark Web in most organizations.
Shifting Left in the Cyber Kill Chain
As with any incident, time is always of the essence. Where possible, organizations need to pinpoint insider threat activity during reconnaissance, the first stage of the cyber kill chain, to successfully mitigate against a malicious actor. Logic dictates that the earlier, or further to the left in the kill chain, that threat actors can be identified, then the less likely they are to be successful in their attack.
Organizations understand the need for preparedness, shielding their borders, and educating their employees. However, these are simply a solid foundation of security infrastructure that requires augmenting with intelligence to stop threats earlier. Dark Web threat intelligence should be considered as an integral component to enhancing an organizations’ security posture. As most cybercriminals rely on Dark Web infrastructure to conduct their operations, cutting off this channel can vastly reduce the chance of insider threats taking hold and disrupting business operations.









