A phishing kit has been found running on at least 700 domains – and mimicking services via false SharePoint, OneDrive and Office 365 login portals.
A newly-uncovered phishing kit, dubbed LogoKit, eliminates headaches for cybercriminals by automatically pulling victims’ company logos onto the phishing login page. This gives attackers the tools needed to easily mimic company login pages, a task that can sometimes be complex.
Cybercriminals have relied on LogoKit to launch phishing attacks on more than 700 unique domains over the past 30 days (including 300 in the past week). These targeted services range from generic login portals to false SharePoint, Adobe Document Cloud, OneDrive, Office 365, and cryptocurrency exchange login portals.
“With LogoKit’s intended functionality to be centered around singular emails per URL and extracting company logos, this dramatically improves ease of carrying out targeted attacks against organizations; and reusing pretexts without changing templates,” said Adam Castleman, security researcher with RiskIQ on Wednesday.
Phishing Kits
Phishing kits, which can be purchased by cybercriminals for anything between $20 and $880, require little technical knowledge to operate beyond modest programming skills. These kits are utilized to steal various data from victims – including usernames, passwords, credit card numbers, social security numbers and more.
In order to operate a kit, a cybercriminal must first install it on a remote server – either by compromising a legitimate content management system, or by utilizing their own infrastructure. Once installed, an attacker merely spams victims – via email messages, SMS or social media messages – with the URL that will take them to the phishing kit’s landing page. Some phishing kits contain administrator dashboards where cybercriminals can track the number of visits to their malicious website and view the sensitive data disclosed.
Phishing kits are nothing new – however, LogoKit makes the deployment of phishing login pages even easier for cybercriminals. Many times, cybercriminals that use phishing kits on top of compromised, legitimate content management systems deal with complex website layouts and multiple files. This could lead to glitches in the login page that serve as potential red flags for victims.
LogoKit skips over this problem with its simplicity, said researchers, as it executes only a few lines of customizable JavaScript. This allows bad actors to easily integrate the kit into either existing HTML pretext templates or build simple login forms to mimic corporate login portals.
The kit also stands out in that it has the ability to load resources from trusted sources, including legitimate object storage buckets. This is another trick that’s not necessarily brand new – but that makes fake login pages appear less malicious by having users navigate to a known domain name.
In some cases, for instance, attackers have been observed hosting their phishing pages on Google Firebase as part of the LogoKit attack. Google Firebase is a mobile and web application development platform that is backed by Google Cloud Storage and provides secure file uploads and downloads for Firebase apps.
How It Works
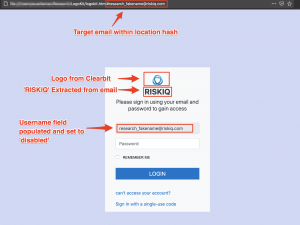
While LogoKit has been found using these legitimate hosting services, researchers have also observed compromised web sites – many running WordPress — to be hosting LogoKit variants. In both cases, cybercriminals send victims a specially crafted URL containing their email address. An example of a crafted URL that contains the email would be: “phishingpage[.]site/login.html#[email protected].”
“The location hash is then broken down into slices,” according to researchers. “The slice’s delimiter is the ‘@’ symbol, allowing the script to extract the user’s/company’s domain to fetch the logo and eventually redirect a victim.”
If victim clicks on the URL, LogoKit then fetches the company logo from a third-party service, such as marketing data engine Clearbit or Google’s database for favicons (the graphic icons associated with particular webpages).
The victim’s email is also auto-filled into the email or username input field of the login graphic. Researchers noted, this trick makes victims believe they have previously logged into the site.
Should a victim enter their password, LogoKit performs an AJAX request, sending the target’s email and password to an external source.
In some cases, as an added trick, after performing validation to ensure data is entered and a valid email address is present, the kit will “fake a user out” by telling them that their password is incorrect and prompting them to enter the password again. Then, as a final step, the victim is redirected to their corporate website after entering their password.
Several sectors have been targeted by attackers using LogoKit, including financial, legal, and entertainment, said researchers.
“The LogoKit presents a unique opportunity for attackers, allowing for easy integration into either existing HTML pretext templates or building simple login forms to mimic corporate login portals,” said Castleman. “Also, with the flexibility of either leveraging compromised infrastructure, attacker-hosted infrastructure, or object storage, attackers can quickly change their delivery source.”
Download our exclusive FREE Threatpost Insider eBook Healthcare Security Woes Balloon in a Covid-Era World , sponsored by ZeroNorth, to learn more about what these security risks mean for hospitals at the day-to-day level and how healthcare security teams can implement best practices to protect providers and patients. Get the whole story and DOWNLOAD the eBook now – on us!