Researchers from the Israeli company ClearSky talked about the hacker group CryptoCore , active since 2018 and specializing in hacking cryptocurrency exchanges.
According to experts, the group is based somewhere in Eastern Europe, and so far it has managed to “earn” more than $ 200,000,000 in compromising exchanges in different countries of the world.
CryptoCore is associated with at least five successful hacks, as well as attempts to attack another 10-20 cryptocurrency platforms. So, five confirmed victims of hackers are in the United States, Japan and the Middle East. Unfortunately, the names of the affected companies were not disclosed due to non-disclosure agreements between researchers.
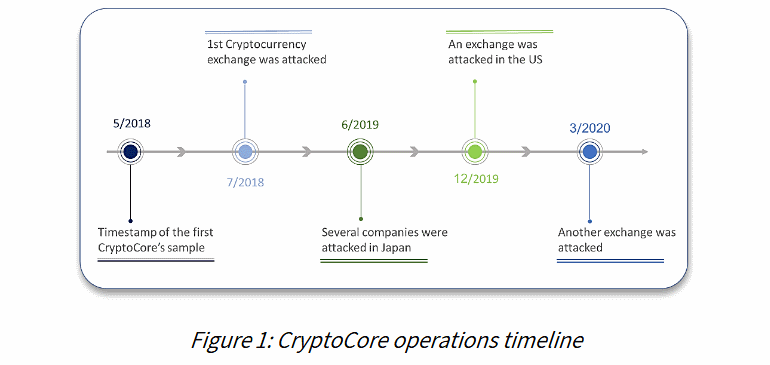
Analysts say they are not the first to discover the group. Earlier, some CryptoCore operations already fell into the reports of other information security companies, for example, Dangerous Password and Leery Turtle . But, as it now turns out, grouping operations were more ambitious and widespread and were not limited to these individual documented cases.
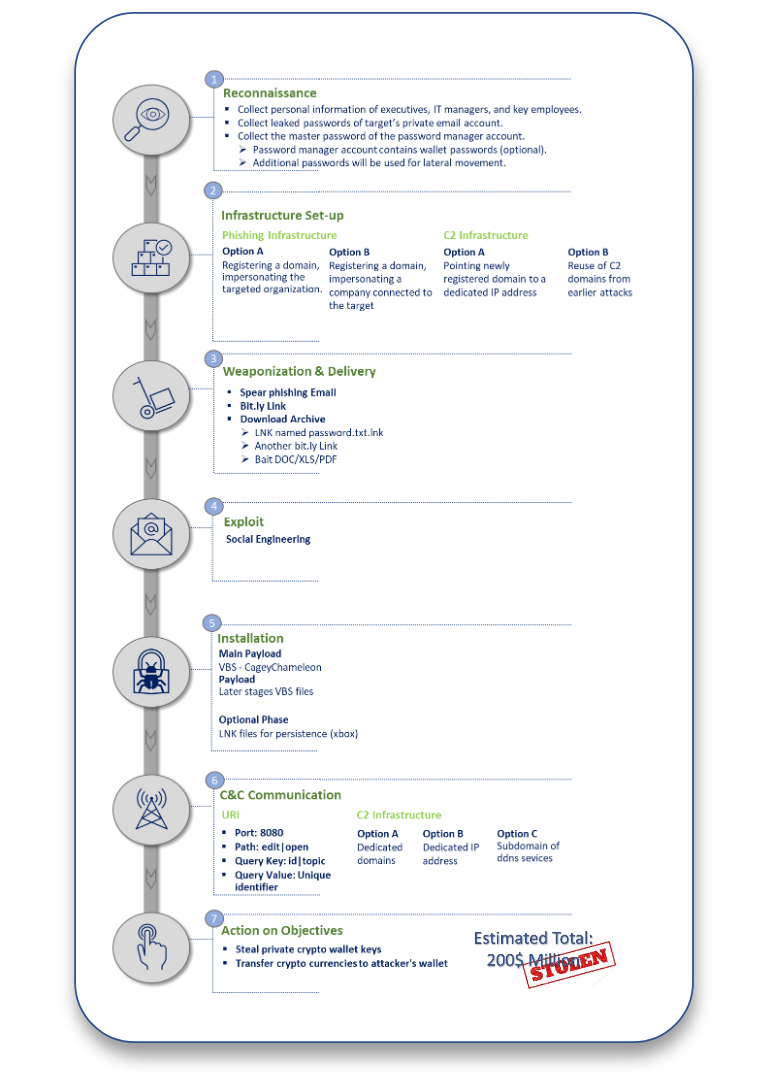
Although ClearSky has been active for two and a half years, hackers have been using the same tactics with minor corrections all this time. So, all attacks began with the collection of information: attackers collected the necessary data about the management of the exchange, its IT staff and other employees.
Then the group went on to phishing attacks, which at first were always directed to personal rather than corporate email addresses. The fact is that personal mailboxes are usually less secure, but there is a good chance that they still contain some kind of working information. And only after some time (from several hours to several weeks) did the CryptoCore operators still proceed to attacks on the victims’ work accounts.
“As a rule, targeted phishing is carried out by impersonating a senior employee of the target company or another organization (for example, a member of the advisory board) who has a connection with the victim,” the researchers explain.
The ultimate goal of the criminals is to introduce the malware to the exchange employee’s computer and gain access to his password manager account (or password theft). If the compromise is successful, CryptoCore members use these passwords to access accounts and wallets, to disable the two-factor authentication system and transfer funds from the “hot wallets” of the exchange to their accounts.
All this makes CryptoCore the second hack group that has regularly attacked cryptocurrency for the past 3-4 years. However, the main threat to exchanges is still the “government” hackers from North Korea. Let me remind you that, according to the UN, for the period from January 2017 to September 2018, North Korean hackers stole about 571 million US dollars from five Asian cryptocurrency exchanges.











