Security researcher Julian Horoszkiewicz discovered a cmd.exe command line shell vulnerability that could allow arbitrary commands to execute.
In search of new attack vectors allowing the introduction of commands in Windows, Khoroshkevich discovered a problem that he described as a mixture of “command / argument mismatch with directory traversal”. During testing, the researcher used Windows 10 Pro x64 (Microsoft Windows [Version 10.0.18363.836]) and cmd.exe version 10.0.18362.449 (SHA256: FF79D3C4A0B7EB191783C323AB8363EBD1FD10BE58D8BCC96B07067743CA81D5). Surely the attack discovered by Khoroshkevich should work on all versions.
The vulnerability could potentially cause a denial of service, disclose information and execute arbitrary code (depending on the system and the target application). Nevertheless, Microsoft assured the researcher that the “strange behavior” of the command-line interpreter that he discovered was intended functionality and could not be considered a vulnerability.
According to Khoroshkevich, he is a little disappointed that his find will not be assigned the CVE identifier. However, on the other hand, in this case, the researcher is free to do anything with it, so he happily published a PoC exploit on his blog.
Some more context from Julian’s Write-Up
Let’s consider the following command line: cmd.exe /c "ping 127.0.0.1",
whereas 127.0.0.1 is the argument controlled by the user in an application that runs an external command (in this sample case it’s ping). This exact syntax – with the command being preceded with the /c switch and enclosed in double quotes – is the default way cmd.exe is used by external programs to execute system commands (e.g. PHP shell_exec() function and its variants).
Now, the user can trick cmd.exe into running calc.exe instead of ping.exe by providing an argument like 127.0.0.1/../../../../../../../../../../windows/system32/calc.exe, traversing the path to the executable of their choice, which cmd.exe will run instead of the ping.exe binary.
So the full command line becomes:
cmd.exe /c "ping 127.0.0.1/../../../../../../../../../../windows/system32/calc.exe"
The potential impact of this includes Denial of Service, Information Disclosure, Arbitrary Code Execution (depending on the target application and system).
According to some twitter replies to Julian’s original post about the finding another user has found a successful command to pass Parameters.
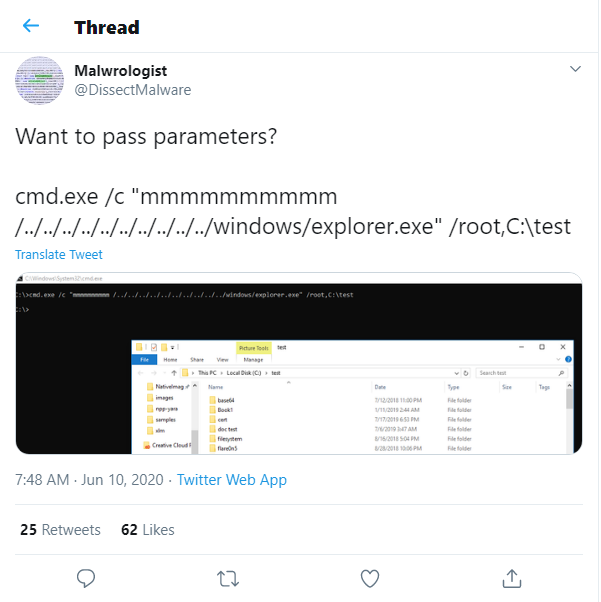
Curious to see what more can be done with this and what will be found. I beleive this can be used with other Microsoft based programs to run power-shell or other malicious commands that may potentially bypass Windows Defender and Anti-Virus. Chained together and embedded in a Macro this can be a lethal attack vector for cyber criminals and hackers. Check Julian’s blog and twitter post for a full write-up and any other future updates and findings.
BLOG: HACKING IS COOL