Author: Sergiu Gatlan
Two high severity security vulnerabilities found in the PageLayer plugin can let attackers to potentially wipe the contents or take over WordPress sites using vulnerable plugin versions.
PageLayer is a WordPress plugin with over 200,000+ active installations according to numbers available on its WordPress plugins repository entry.
Bugs can lead to takeover attacks and wiped sites
The vulnerabilities were reported to PageLayer’s developer by the Wordfence Threat Intelligence team on April 30 and were patched with the release of version 1.1.2 on May 6.
According to Wordfence, the two security flaws can be exploited by attackers to wipe WordPress sites running older unpatched versions of the plugin, as well as launch takeover attacks.
“One flaw allowed any authenticated user with subscriber-level and above permissions the ability to update and modify posts with malicious content, amongst many other things,” Wordfence explains.
“A second flaw allowed attackers to forge a request on behalf of a site’s administrator to modify the settings of the plugin which could allow for malicious Javascript injection.
As further detailed by the researchers, the two bugs are due to unprotected AJAX actions, nonce disclosure, and a lack of Cross-Site Request Forgery (CSRF) protection that make it possible for attackers to inject malicious JavaScript code, alter the attacked sites’ pages, create rogue admin accounts, redirect visitors to malicious sites, and “exploit a site’s user’s browser to compromise their computer.”
More details regarding the two PageLayer vulnerabilities, their impact, and how they were patched by the development team can be found in Wordfence’s report.
To defend against potential attacks, users should immediately update their PageLayer installations to version 1.1.2 which fixes the security issues.
At least 120K sites still exposed to attacks
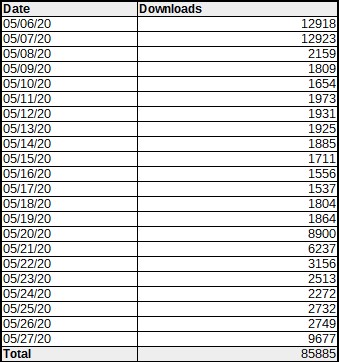
While PageLayer 1.1.2 was released on May 6, it only had just over 85,000 new downloads until yesterday, May 27, including both new installs and updates, according to raw downloads data on the WordPress’ plugin repository.AD
This means that at least 120,000 WordPress sites with active PageLayer installation might be exposed to takeover and wipe attacks in the eventuality that hackers decide to exploit these bugs.
Two weeks ago, Wordfence’s research team also found a critical bug in Google’s official WordPress plugin with 300,000 active installs that could let attackers gain owner access to vulnerable sites’ Google Search Console and exploit it for black hat SEO.
Researchers also discovered stored cross-site scripting (Stored XSS) vulnerabilities in several other WordPress plugins including Real-Time Find and Replace, Ninja Forms, and Contact Form 7 Datepicker with over 1,200,000 active installations that could be used to take over sites and create new admins.













