At the Virus Bulletin 2020 conference , the Facebook security team revealed one of the most challenging malware operations it has ever faced.
The expert report was dedicated to the Chinese hack group SilentFade and its activity from the end of 2018 to February 2019. The main target of these hackers, as you might guess, were Facebook users. The attackers used Windows Trojans, browser injection, scripting, and even vulnerabilities in the Facebook platform for their campaigns. The hackers ‘task was to infect users with a Trojan, take control of their browsers and steal passwords and cookies to gain access to the victims’ social network accounts.
First of all, the hackers were interested in the accounts to which any possible payment method is tied. On behalf of such accounts, SilentFade bought ads on Facebook, of course, using the victim’s means.
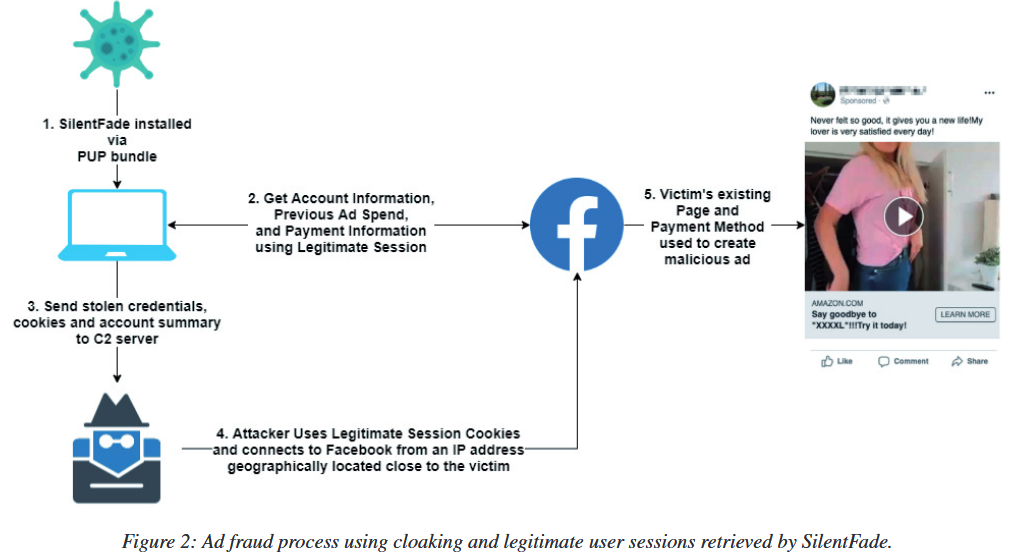
Although the group’s activity lasted only a few months, according to Facebook, during this time the scammers managed to deprive users of more than 4,000,000 US dollars, all of which was used to place malicious ads.
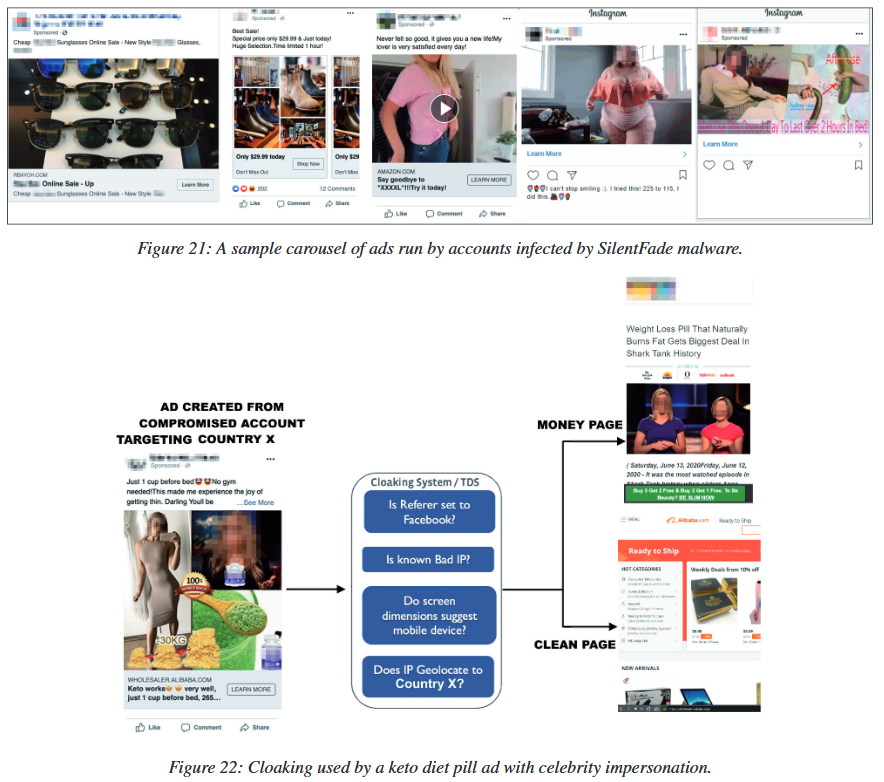
Such ads, as a rule, were limited to the geographic region of the infected user (in order to limit their availability and not attract too much attention), and all were built according to the same template. For example, hackers used short URLs and celebrity images to lure users to various fraudulent sites selling questionable goods, including weight loss aids, keto pills, and more.
Facebook security took notice of SilentFade in February 2019 when users began to complain about suspicious activity and illegal transactions originating from their accounts.
The investigation made it possible to identify the malware used by the cybercriminals, previous strains of the group’s malware, as well as campaigns dating back to 2016. In the end, all this helped to associate suspicious activity with a specific Chinese company and two developers.
According to Facebook, SilentFade began operations in 2016, when a malware called SuperCPA was developed, primarily targeting Chinese users.
“Not much is known about this malware because it was controlled by downloadable configuration files, but we believe it was used for click fraud (CPA stands for Cost Per Action in this case),” said the experts.
Already in 2017, the group decided to abandon the use of SuperCPA, and then the first version of the SilentFade malware appeared. This early version attacked browsers and stole credentials from Facebook and Twitter accounts, focusing on verified profiles and profiles with a large number of followers. However, the hackers did not stop at simple account hijacking, and SilentFade continued to evolve. In fact, the most dangerous version of malware that was used for attacks in subsequent years appeared in 2018.
The researchers reported that the attackers were distributing a new version of SilentFade in conjunction with legitimate software that they posted for download on the Internet. For example, one day Facebook experts stumbled upon an announcement from the SilentFade developers published on hacker forums. The scammers wrote that they were ready to buy traffic from hacked sites and other sources, and after the purchase they redirected it to the pages that hosted various software infected with SilentFade.
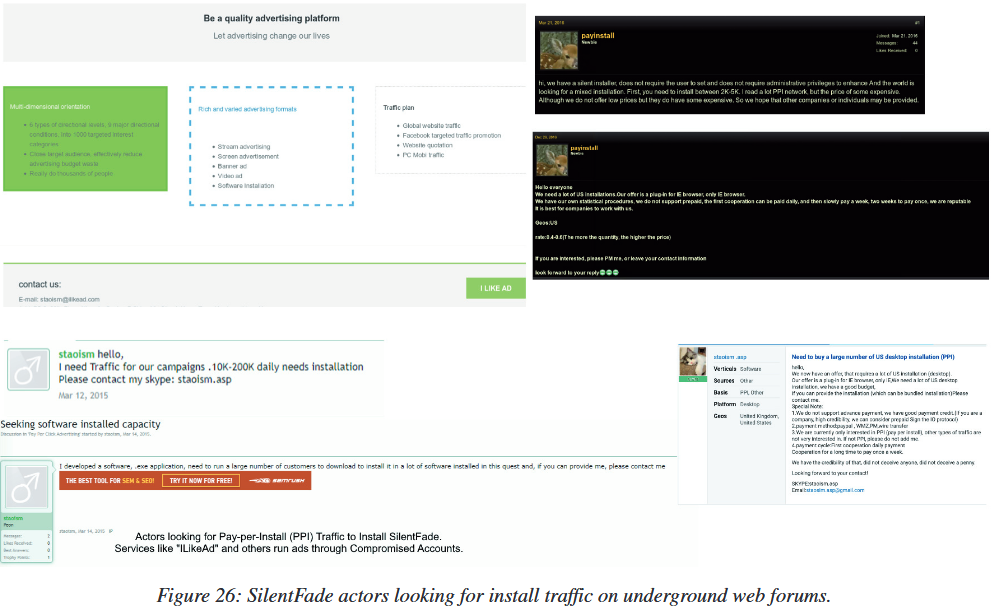
If a user fell for a scammer’s trick and malware entered the system, the SilentFade Trojan gained control over the victim’s computer and replaced the legitimate DLL files of the browser with malicious versions, which, in essence, allowed SilentFade operators to control the victim’s browser. Thus, the malware is able to successfully attack Chrome, Firefox, Internet Explorer, Opera, Edge, Orbitum, Amigo, Touch, Kometa and Yandex Browser.
These malicious DLLs were then used to steal credentials stored in the browser as well as cookies. The hackers used the Facebook session cookies to gain access to the victim’s account, and as a result, they did not need to provide credentials or a 2FA token.
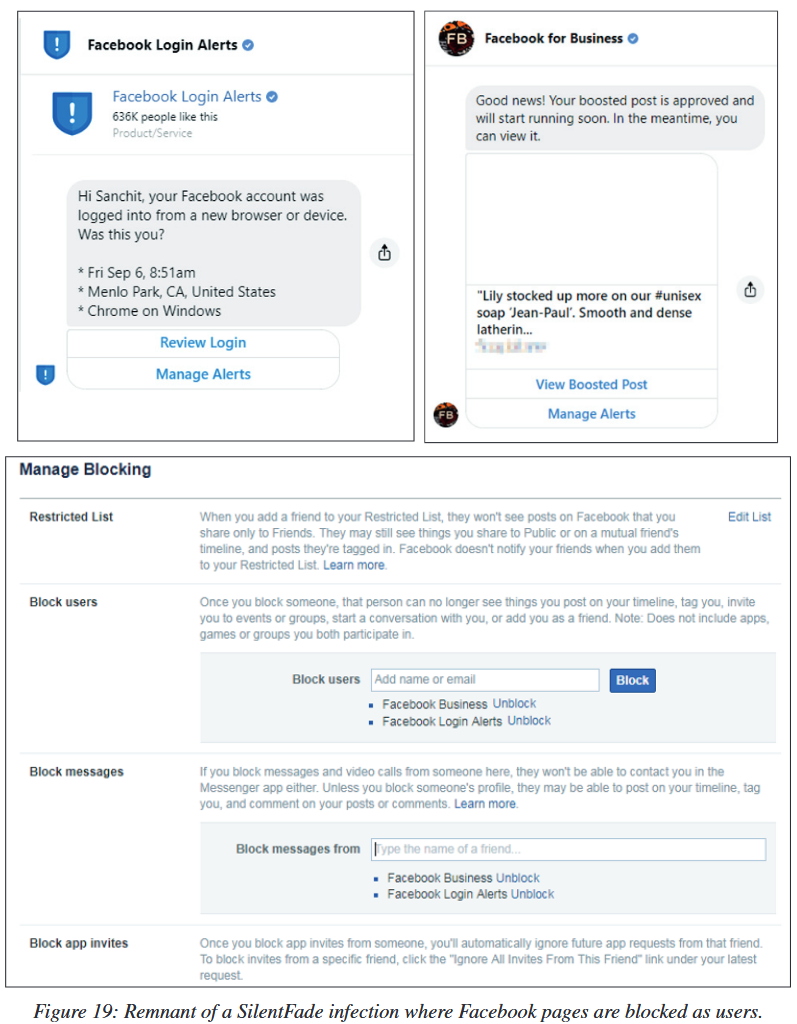
Once access to the user’s account was obtained, the malware used scripts to disable the social network’s security mechanisms. Investigating what is happening, Facebook experts discovered a vulnerability in its own platform, due to which users could not re-enable the deactivated security features.
So that users do not know that someone has compromised their account and is placing ads on their behalf, SilentFade operators used control over the victim’s browser to access the Facebook settings section and disabled:
- site notifications;
- chat notification sounds;
- SMS notifications;
- any email notifications;
- page related notifications.
At the same time, the attackers understood that Facebook’s security systems could still detect suspicious activity and logins, and inform users about this via private messages. Therefore, hackers additionally blocked the Facebook for usiness and Facebook Login Alerts accounts, from which such warnings could come.
The mentioned Facebook bug was abused by hackers every time the user tried to unblock these accounts, provoking the error and preventing the victim from getting rid of these bans.
“This is the first time we’ve seen malware actively altering notification settings, blocking pages, and exploiting a bug in the blocking subsystem to secure a foothold in a compromised account.
However, the exploitation of the notification bug was even a positive development. This allowed us to identify compromised accounts, assess the scale of SilentFade infections and correlate this data with user account abuse, linking it to the malware responsible for the initial compromise of the accounts, ”the researchers said.
As a result, in 2019, Facebook engineers fixed the found bug, canceled all malware actions to block notifications, and compensated the damage to users whose accounts were used to buy malicious ads.
But the company’s specialists did not stop there: throughout 2019, they tracked the malware itself and its creators all over the Internet. So, they managed to find an account on GitHub that hosted many libraries that were clearly used to develop SilentFade.
This account was linked by experts to the Hong Kong-based development company ILikeAd Media International Company Ltd., established in 2016, and the two people who founded it, Chen Xiao Kong and Huang Tao.
As a result, in December 2019, Facebook filed a lawsuit against this company, and the proceedings are still ongoing.
In their report, Facebook experts emphasized that SilentFade is only part of a major trend among cybercriminals. It turned out that many hackers living in China are increasingly targeting the social network and its 2,000,000,000 users. Specifically, Facebook is attacked by Mavlar such as Scranos , FacebookRobot and StressPaint .