Several government computers were wiped using the novel WhisperGate malware in a coordinated attack against Ukraine.
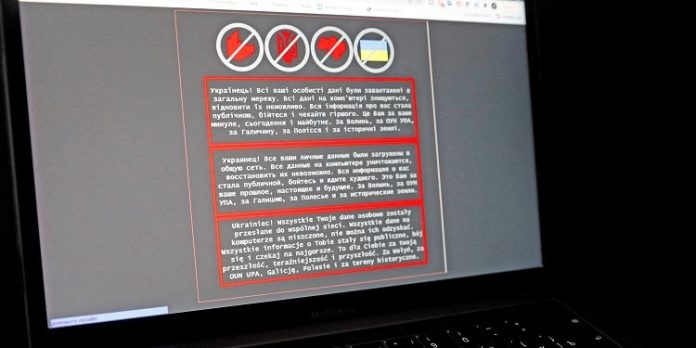
Last week Ukraine was hit with a massive cyberattack, affecting the websites of the foreign ministry, education ministry, ministry of agriculture, energy, and sports ministries have been hit, as well as that of the state emergency service.
Further investigation by Microsoft revealed that threat actors also deployed destructive malware, dubbed WhisperGate, in systems belonging to several Ukrainian government agencies and organizations that work closely with the Ukrainian government.
No group took the blame after the attack. However, Ukrainian officials point to Russia and Belarus, a close ally of Moscow, as culprits behind the intrusion.
While the Friday attack focused on defacing government websites, journalist Kim Zetter confirmed that several government computers were wiped by WhisperGate malware.
According to Zetter, the malware wiped seven workstations at one government agency and several workstations and servers at another. Since the destruction of data happened simultaneously, officials believe it was a coordinated action.
Coordinated attack
Ukrainian Cyberpolice believes that the Friday attack is a lot more complex than simple website modification.
“A number of external information resources were destroyed by the attackers manually. The short deadlines for the attack indicate the coordination of hackers’ actions and their number,” Ukrainian authorities claim.
Cyberpolice identified that threat actors employed at least three attack vectors: supply chain attack via IT infrastructure partners, exploitation of content management system OctoberCMS, and Log4j vulnerability.
Apache Software Foundation disclosed Log4j, the remote code execution (RCE) vulnerability in Apache Log4j, also known as Log4Shell, on December 10.
Ukrainians also claim that the Friday attack also involved a distributed denial-of-service (DDoS) attack against government agencies. The source of the attack is yet to be identified.

Echoes of the past
The US Cybersecurity and Infrastructure Security Agency (CISA) issued an advisory on January 18, urging US organizations to stay alert in the light of cyberattack against Ukraine.
“The identification of destructive malware is particularly alarming given that similar malware has been deployed in the past—e.g., NotPetya and WannaCry ransomware—to cause significant, widespread damage to critical infrastructure,” CISA warned.
NotPetya and WannaCry malware attacks cost up to $20 billion in damage and affected numerous nations and organizations all over the world.
Researchers at Stairwell, a cybersecurity company, draw parallels between WhisperGate malware and the hacking of the Ukrainian power grid in December 2015, which resulted in nationwide power outages for over 230,000 consumers.
The power grid attack was attributed to threat group Sandworm, also known as Voodoo Bear, linked with a Russian foreign intelligence service GRU.
Previous Sandworm attacks also imitated ransomware attacks without a crucial element of ransomware – a mechanism for data recovery.
Invisible stage
While the original analysis of WhisperGate by Microsoft named two stages for malware deployment, researchers at Stairwell think there might be a third one.
Stage 1 of WhisperGate deploys master boot record (MRB) ransomware. The file named stage1.exe has a build timestamp of January 10, 2022.Once executed with admin permission, the program will present a ransom note after a system reboot.
Stage 2 of the malware, a loader named stage2.exe, was built 2 minutes after stage one on January 10. The loader downloads and loads into memory a payload retrieved from Discord’s content delivery network (CDN).
The third stage, researchers at Stairwell claim, has initially been clustered as part of stage 2 in the Microsoft post, is significantly more complex.
SentinelOne researcher Juan Andres Guerrero-Saade was one of the first to identify a copy of stage 3 files. In a nutshell, stage 3 will overwrite files on a system with specific extensions, wiping the whole system.
“With many unknowns, such as the intrusion vector, reported Linux variants, and the pace with which events can potentially escalate from cyber to traditional military actions, it’s clear that faster identification and analysis will become paramount in the days to come,” the report’s author claims.
More from CyberNews:
Troubling trend: it takes nine months to detect and respond to a cyberattack
Microsoft to buy Activision for $68.7 billion in gaming push
Earth Lusca: cyber espionage with crypto theft on the side
Scammers set up a mock Nintendo site peddling phony discounts
Subscribe to our newsletter